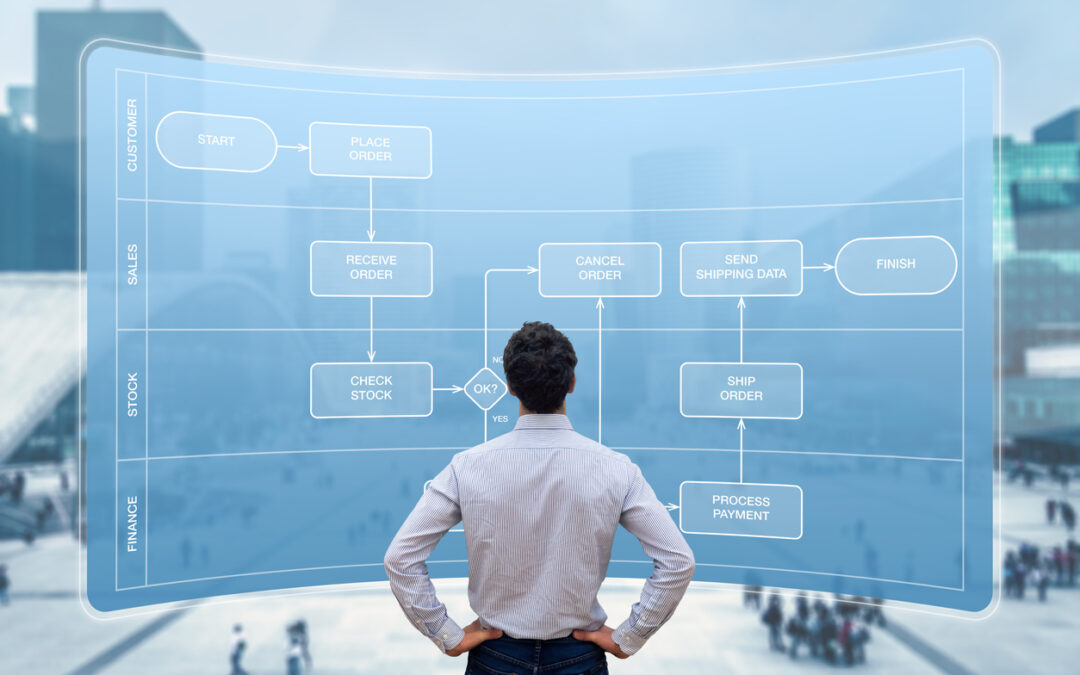
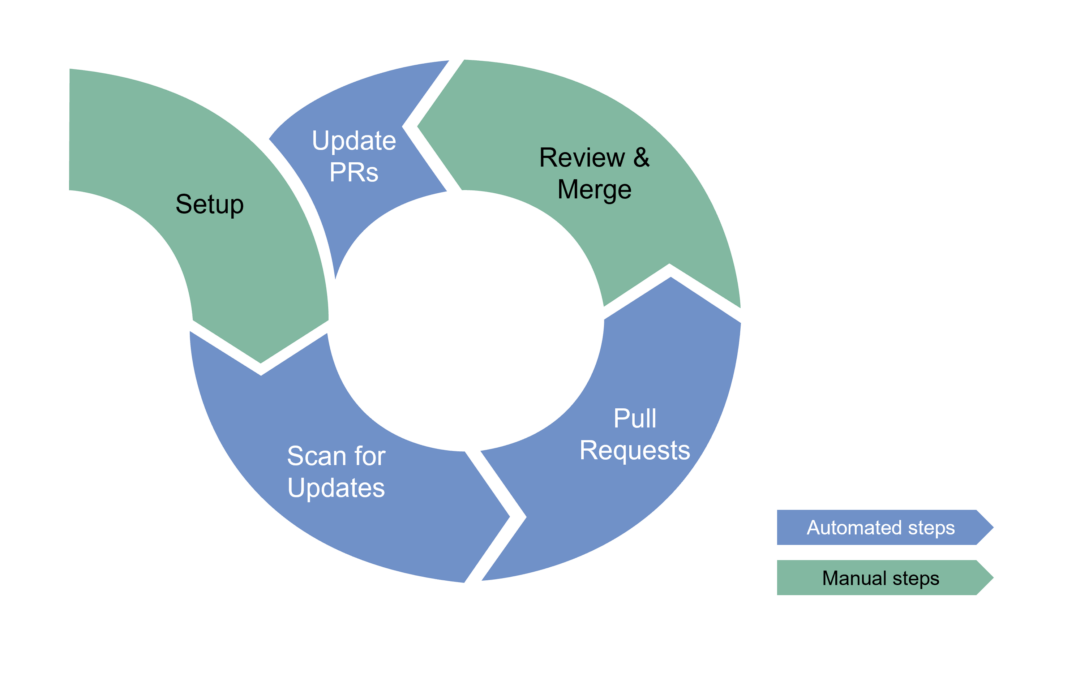
In today’s fast-evolving digital landscape, software isn’t just a collection of functions performing specific tasks – in fact it’s a web of interwoven workflows that dictate how systems interact and respond to dynamic business needs. Julian and Philipp dive into the topic of workflow orchestration and their experience how software products can be improved with workflow engines such as Camunda.