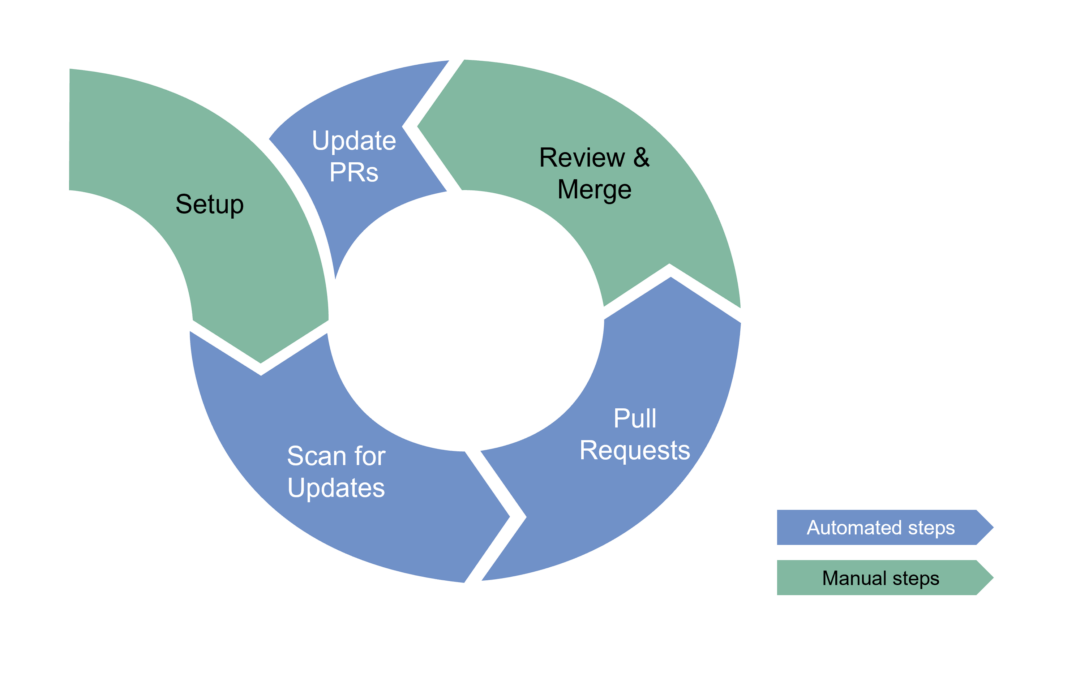
In today’s interconnected and rapidly evolving software landscape, vulnerabilities are an unavoidable part of development. As the complexity of applications grows, so does the attack surface. With dependencies on numerous external libraries, open-source packages, and container images, transitive CVEs become one of the most common vulnerability findings and worth focusing at. This blog post will introduce you the the world of CVE Management and give you an overview of some common tools you might use.